If you’re using Azure Logic Apps to automate your workflows, you might want to secure your communications by running them inside a virtual network (VNet). A VNet provides a private and isolated environment where your Logic Apps can connect to your on-premises resources or other resources running in Azure, such as VMs or databases.
In this post, I’d like to share a solution we found when working with a VNet alongside a Logic App and Azure Storage using Private Endpoints. While the issue might seem common and simple, we found the information online not to be very clear. Therefore, I hope to shed some light on the solution in this article.
For the main part you can follow the Microsoft guide here: Deploy Standard logic apps to private storage accounts – Azure Logic Apps | Microsoft Learn.
Connect to storage behind Private Endpoints
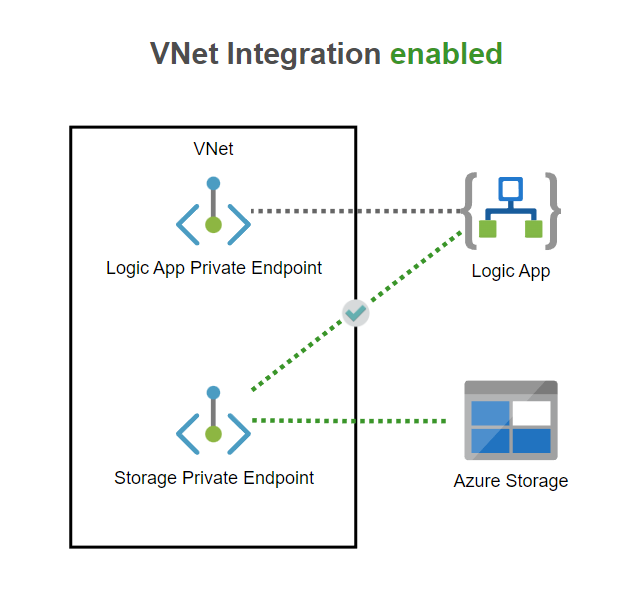
Assuming you have a Logic App and want to use private storage it’s important to notice that you will need VNet integration for that. It’s a common misunderstanding that configuring a Private Endpoint for your Azure Resource makes it a part of your VNet. This is not the case! Your resource can receive requests from the VNet, but that’s only one way. The same goes with a Logic App behind a Private Endpoint, it doesn’t allow the Logic App to communicate with the VNet, so to make private storage possible, you will need to enable VNet integration on outbound traffic on the Logic App.
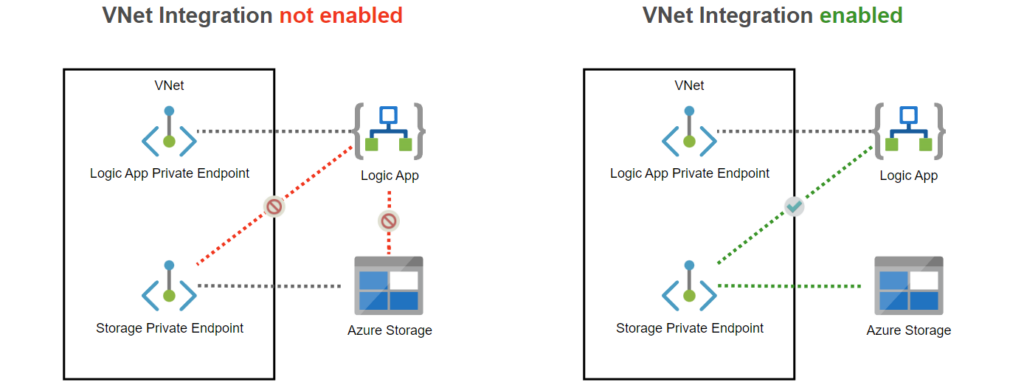
So, make sure you enable VNet Integration on the Logic App.
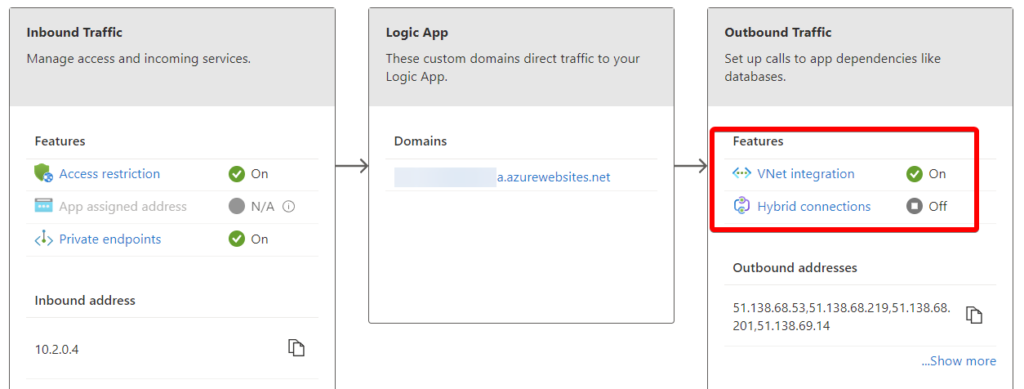
Necessary Logic App Configuration settings
After enabling the VNet Integration there are still some properties that need to be set manually for the Logic App to work. Under the Configuration tab add the following properties.
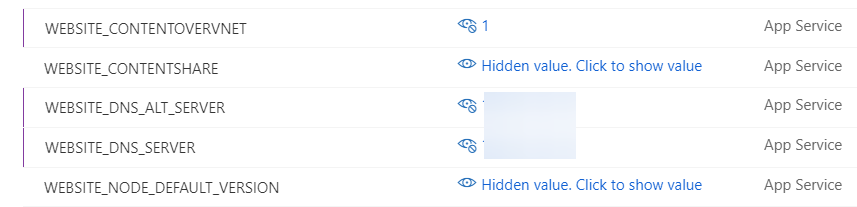
...
{
"name": "WEBSITE_CONTENTOVERVNET",
"value": "1",
"slotSetting": false
},
{
"name": "WEBSITE_DNS_SERVER",
"value": "xx.xx.xx.xx",
"slotSetting": false
},
{
"name": "WEBSITE_DNS_ALT_SERVER",
"value": "xx.xx.xx.xx",
"slotSetting": false
},
...
Use your primary and secondary private DNS here if the infra is configured with a private DNS. If you haven’t explicitly configured a private DNS you may need to use Microsoft Azure’s magical virtual IP 168.63.129.16 as the primary and secondary DNS server. More about this address here: What is IP address 168.63.129.16? | Microsoft Learn.
NB: Always use the private DNS servers if those are available, because company’s often block Microsoft’s 168.63.129.16 IP.
That’s it
Enjoy your secured Logic App with private storage over Private Endpoints.
Common problems
Error: System.Private.CoreLib: Access to the path ‘C:\home\site\wwwroot\host.json’ is denied.
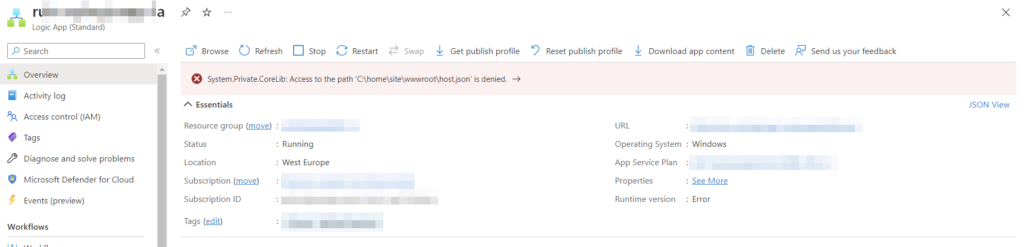
When this error occurs it means that your Logic App cannot connect to your storage account. Make sure that VNet Integration is enabled and the configuration settings are set correctly. Also double-check the DNS configuration, make sure you’re using the appropriate DNS servers for the VNet.
Error: Cannot reach host runtime. Error details, Code: ‘BadRequest’, Message: ‘Encountered an error (InternalServerError) from host runtime.’
The Logic App uses the File Share protocol of Azure Storage. So make sure the following things are in place:
- Private Endpoint for the File subtype is enabled and working properly
- The WEBSITE_CONTENTAZUREFILECONNECTIONSTRING property is configured properly
- The file share configured in the WEBSITE_CONTENTSHARE property does exist and is available as a file share under the Storage Account (via Storage Browser).
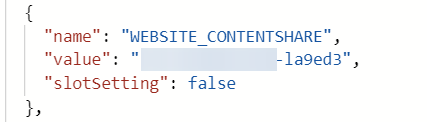
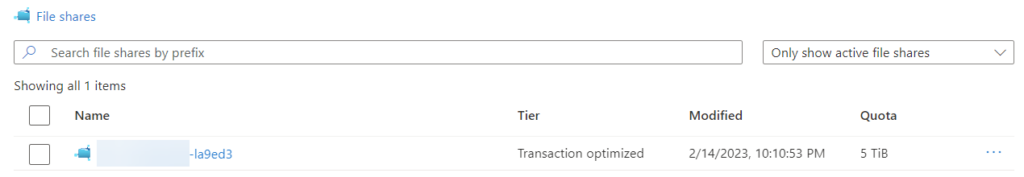
This error can be caused by a wide variety of issues, one of them might be a wrongly configured workflow that is being deployed.

Leave a Reply